CrowdStrike 101:
CrowdStrike is a next-gen, cloud-native endpoint cybersecurity company. Its bread-and-butter is called endpoint detection and response (EDR), which replaces legacy anti-virus (AV). Beyond EDR, it offers applications in cloud security, log management, forensics, identity, data protection etc. to round out its “Falcon Platform.” Falcon’s edge is in its ability to digest near-endless amounts of data to automate and uplift breach protection. CrowdStrike uses its large and diverse dataset to constantly improve Falcon’s efficacy and use cases… all with a single console and single agent to ensure superior interoperability. It can recycle this same data over and over again to efficiently develop new products for a single interface. More utility without adding complexity.
Important Endpoint Security Acronyms:
- Endpoint detection and response (EDR) provides end-to-end visibility and protection with automated remediation and flagging services.
- Managed detection and response (MDR) encompasses CrowdStrike’s team of threat hunters to augment EDR with human touch when needed.
- Extended detection and response (XDR) is EDR with 3rd party, non-endpoint data sources infused. The incremental data sharpens breach protection and extends it beyond the endpoint.
Important Log Management Acronyms:
- Log Scale ingests, organizes and stores data logarithmically. This allows for ingestion with more scale and faster time to value. As an important aside, Log Scale is a key ingredient for Falcon XDR. It is instrumental in XDR onboarding needed data sources in a scalable and efficient manner. This can be used to improve security and other parts of operations too.
- Security Information and Event Management (SIEM) aggregates security logs/data to help organizations uncover and remediate threats faster. Log Scale is closely related to SIEM, as Log Scale is what actually collects data from various sources to be utilized here.
Important Cloud Security Acronyms:
- Cloud Security & Posture Management (CSPM) tells you about your vulnerabilities and misconfigurations.
- Cloud Infrastructure Entitlement Management (CIEM) tells you who is entering a software environment. It tells you if these entrants are allowed and exactly what they’re allowed to do.
- Cloud Workload Protection (CWP) is a preventative measure to observe if anything bad is being done by entrants. This sounds the alarm bell while preventing and remediating cloud infrastructure attacks. It’s closely related to CSPM and CIEM.
- Cloud Native Application Protection Platform (CNAPP) is the overall suite tying all of these cloud products together.
- Application Security Posture Management (ASPM) locates and facilitates the safe control of cloud apps.
Now let’s dig into the detailed quarterly review:
a. Demand
- Beat revenue estimates by 1.8% & beat guidance by 1.9%.
- Subscription revenue rose by 34% Y/Y.
- Beat annual recurring revenue (ARR) estimates by 0.6%. Net new ARR (NNARR) estimates beat by about 5%-10% depending on the source. Most indicate the beat was closer to 10%. Regardless, really good.
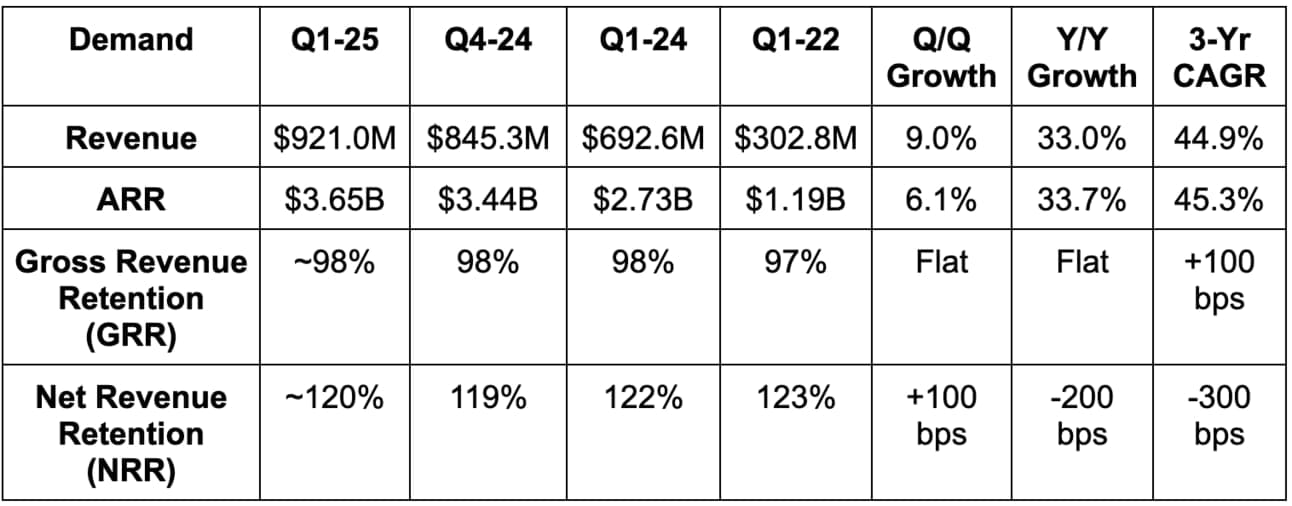
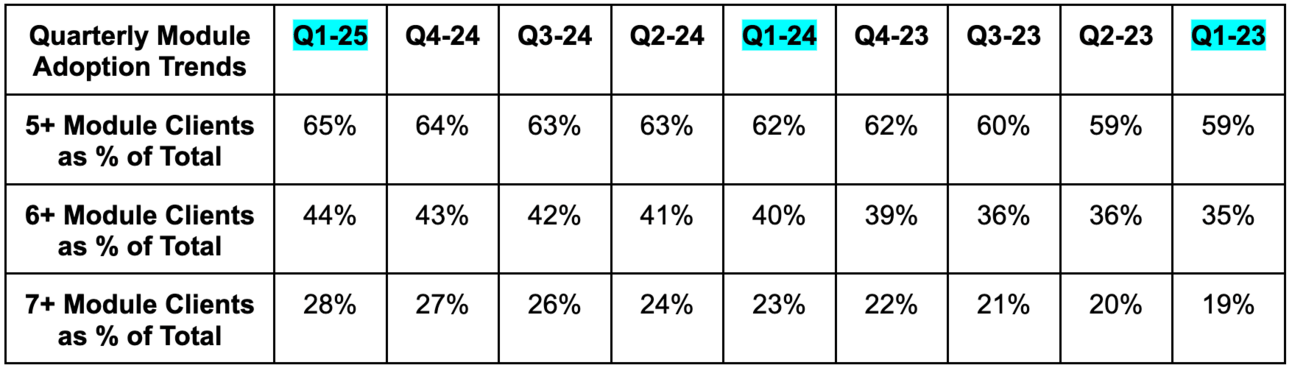
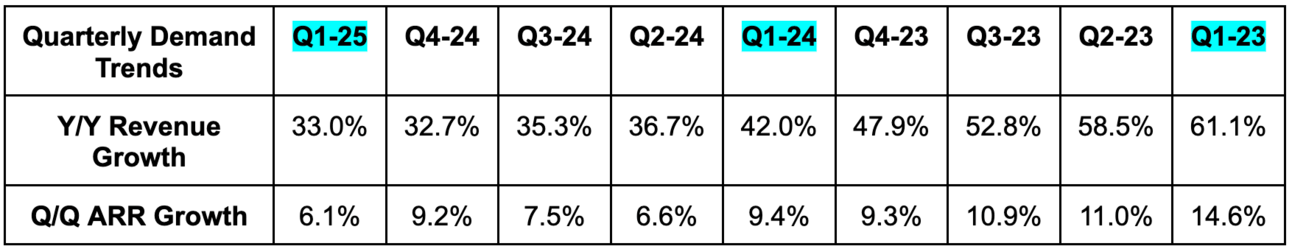
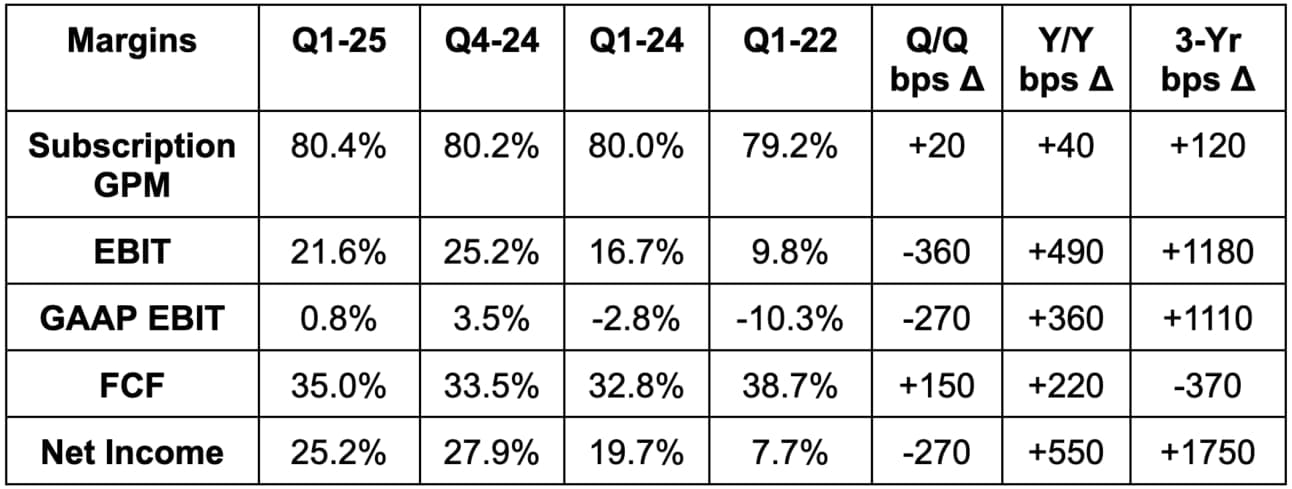
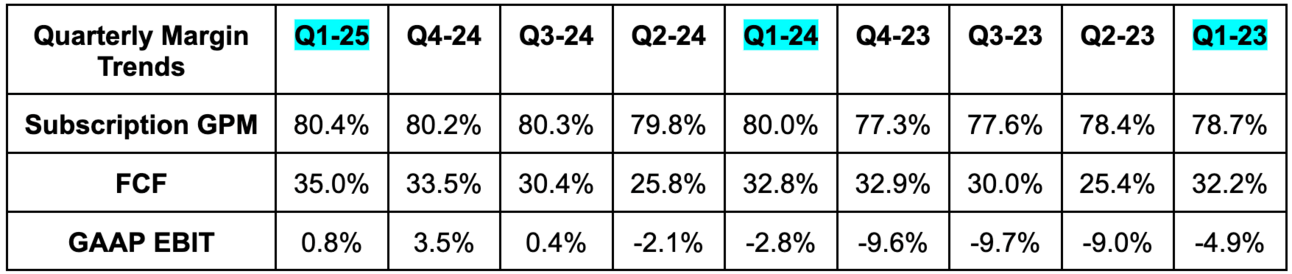
b. Profits & Margins
- Beat 78% non-GAAP gross profit margin (GPM) estimates by 30 basis points (bps; 1 basis point = 0.01%).
- Beat free cash flow (FCF) estimates by 4.0%. FCF rose by 41.7% Y/Y.
- Beat EBIT estimates by 4% & beat EBIT guidance by 4.9%.
- Beat $0.89 EPS estimates by $0.04 & beat EPS guidance by $0.03. EPS rose by 63% Y/Y.
- Met $0.17 GAAP EPS estimates. $0.17 in GAAP EPS compares to $0.00 Y/Y.
This is its 5th straight quarter of GAAP profitability. Its entrance into the S&P 500 is inevitable in my view. When not if.
c. Balance Sheet
- $3.7 billion in cash & equivalents.
- $742 million in traditional debt.
- Diluted share count rose by 3.9% Y/Y. The team reiterated expectations for 3.0% Y/Y dilution this year. Important.
CrowdStrike continues to lean back into hiring and growth investments. Headcount rose by 15% Y/Y. Leverage is regardless of this added spend appetite.
d. Annual Guidance & Valuation
- Raised annual revenue guidance by 1%, which beat estimates by 0.5%.
- Raised annual EBIT guidance by 7.0%, which beat estimates by 6.0%.
- Raised $3.92 EPS guide by $0.06, which barely beat estimates by $0.01.
- Reiterated guidance calling for a 32% FCF margin for the year.
- Next quarter guidance is ahead across the board. It sees 10%-15% NNARR growth next quarter.